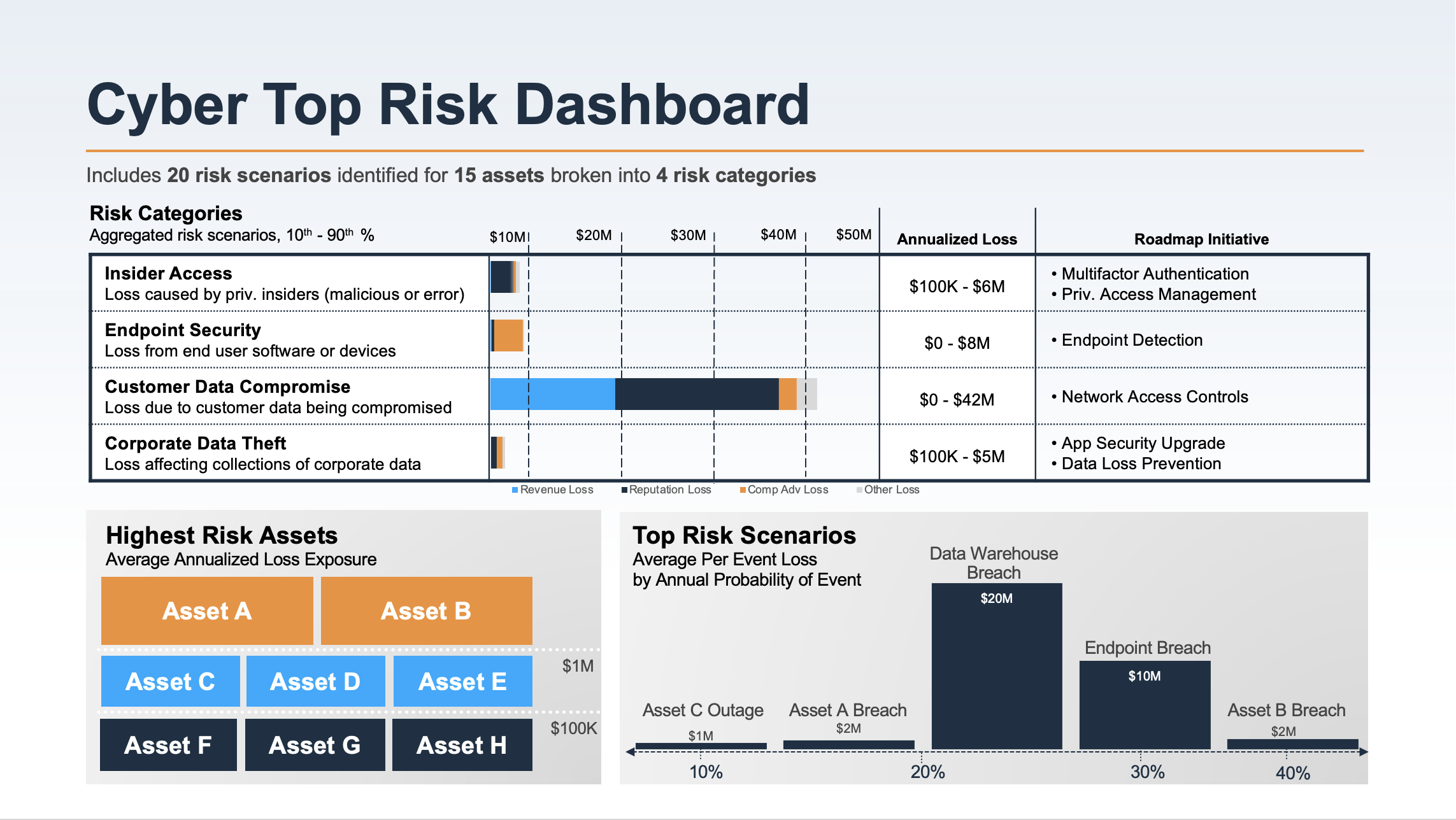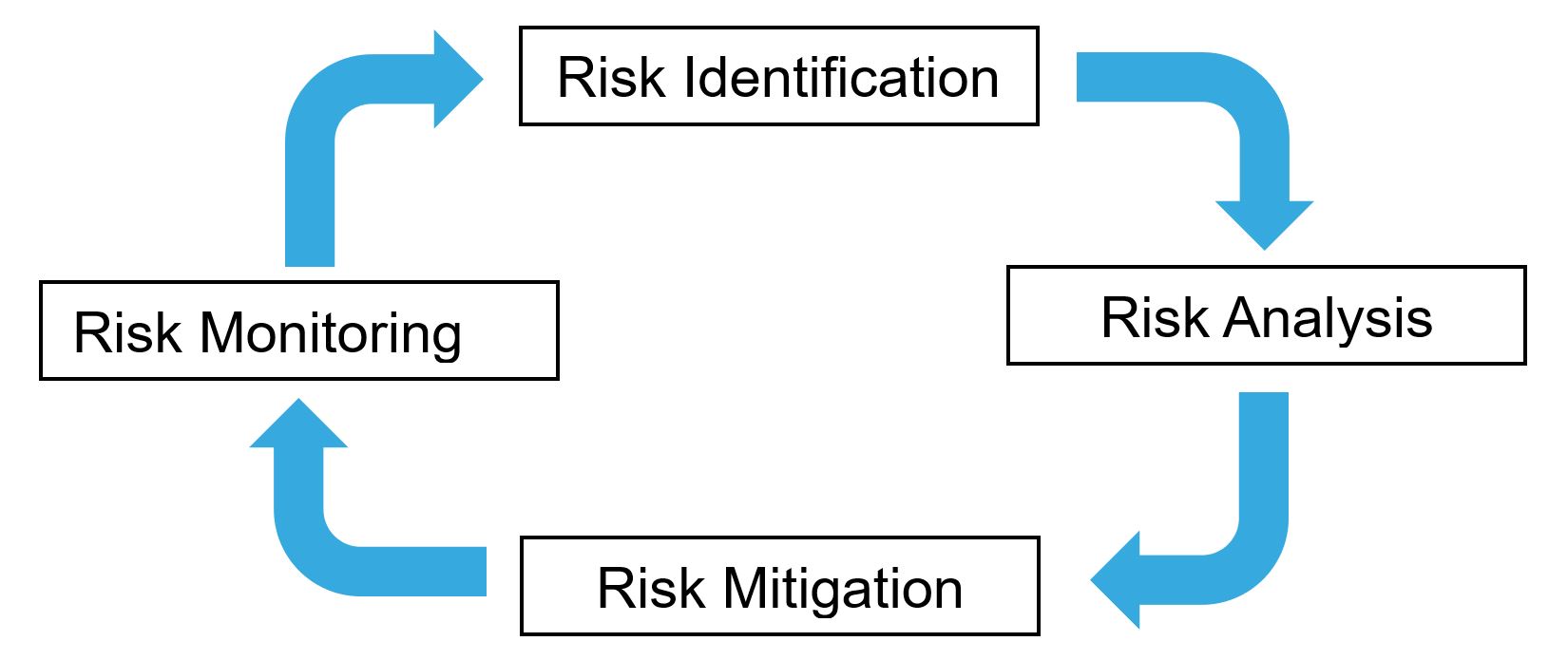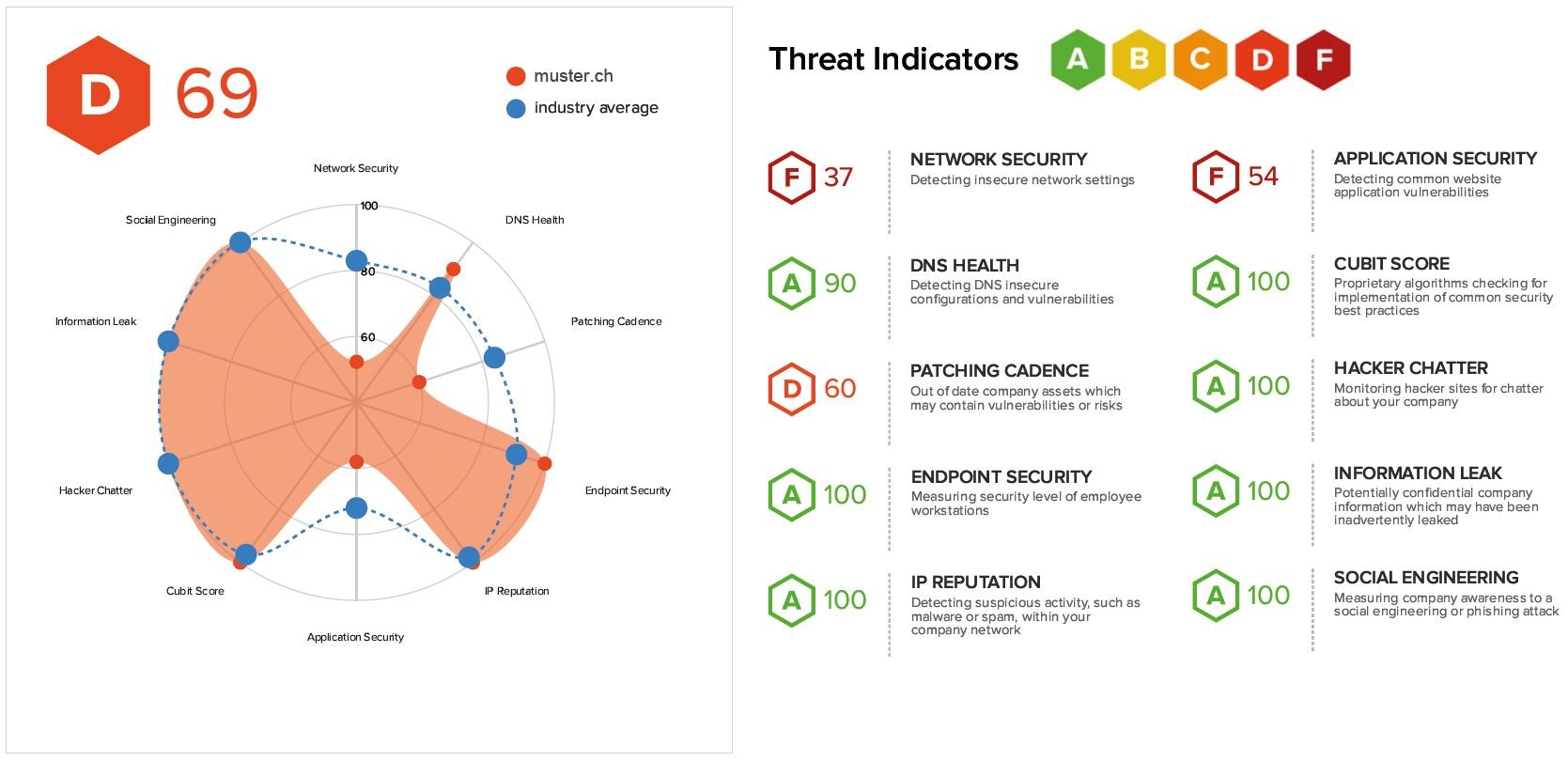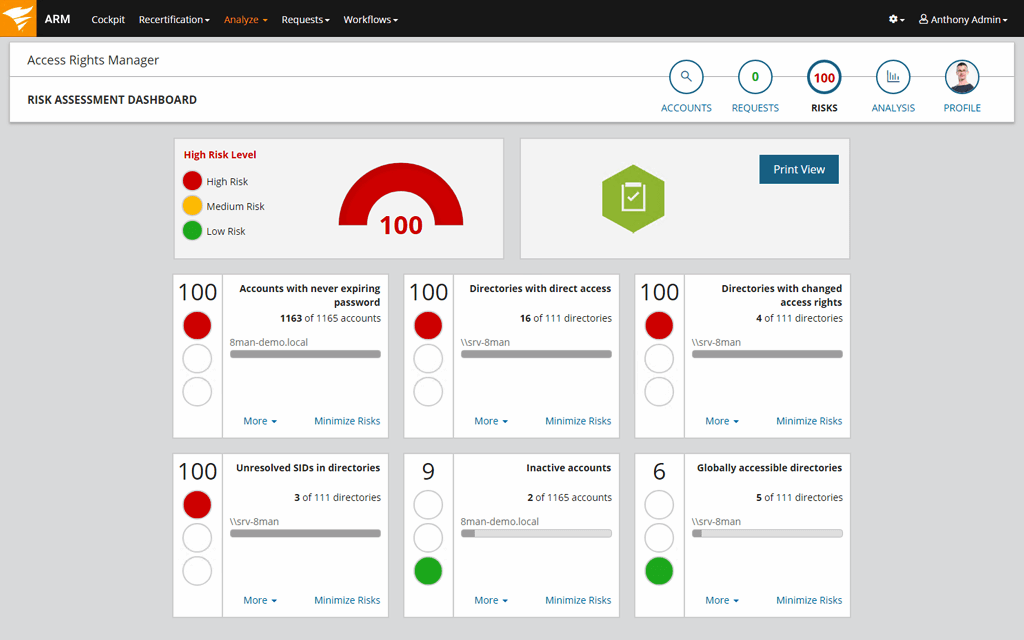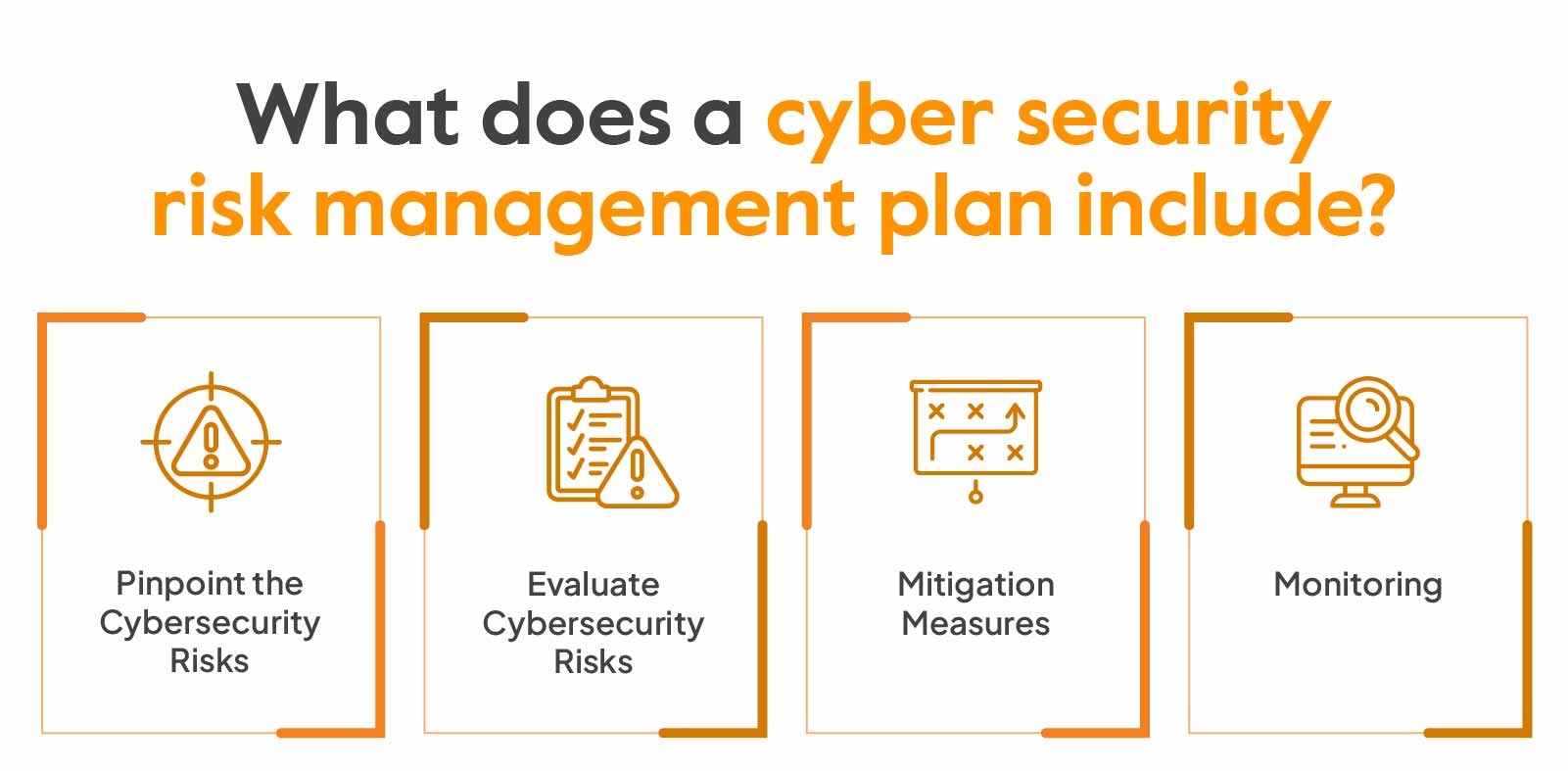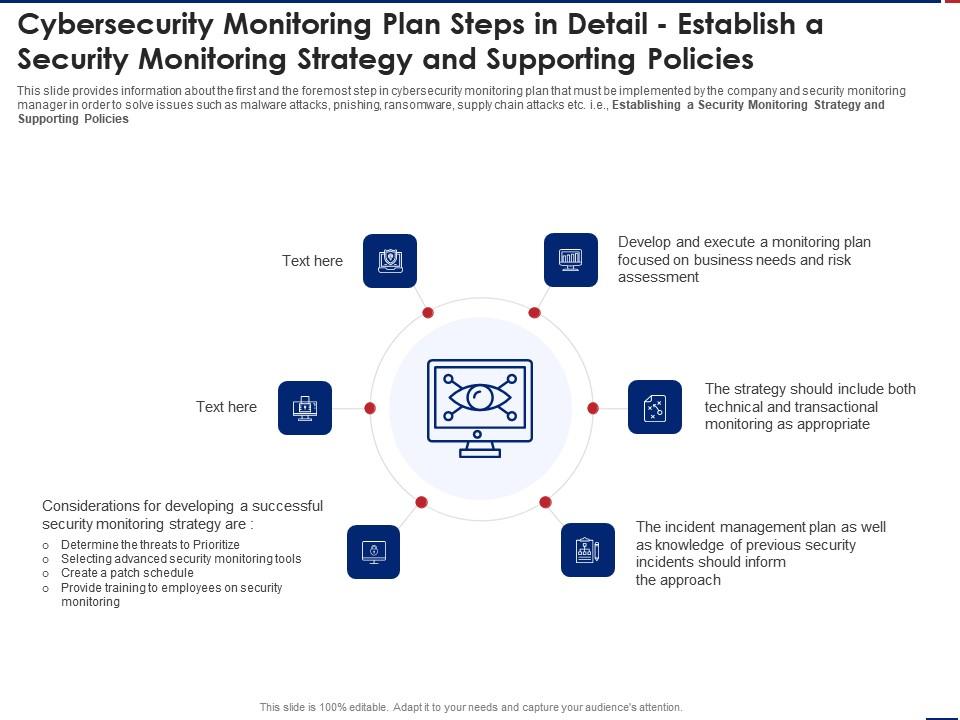
Effective Security Monitoring Plan Cybersecurity Monitoring Strategy Ppt Pictures | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Systemic cyber risk management for enterprise network. The asset owner... | Download Scientific Diagram

Avetta Launches Cyber Risk Solution to Give Companies 24/7 Visibility of Cybersecurity Risks in Their Supply Chain | Avetta | AU