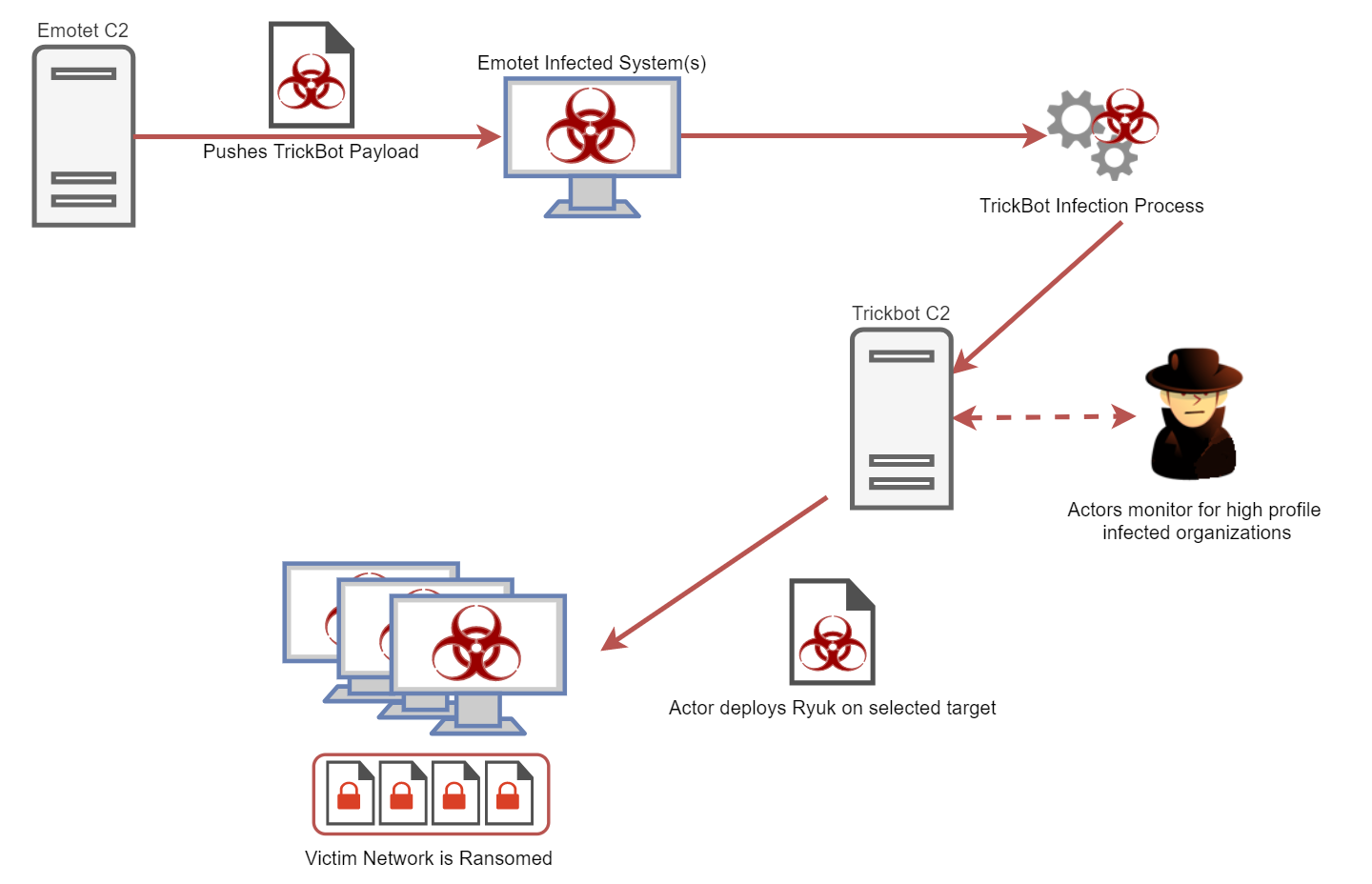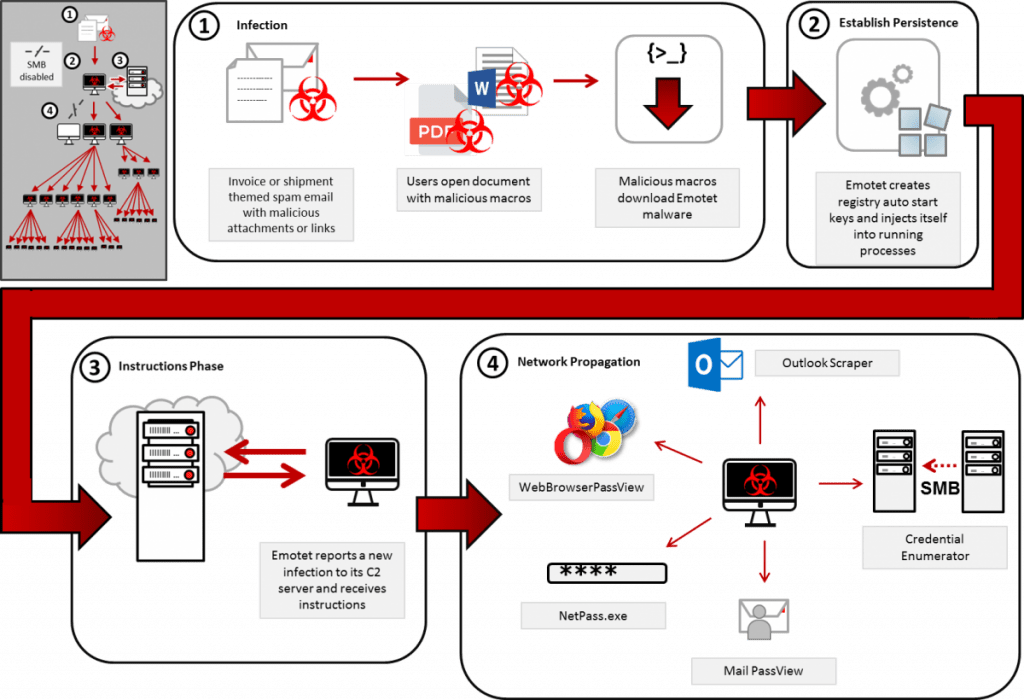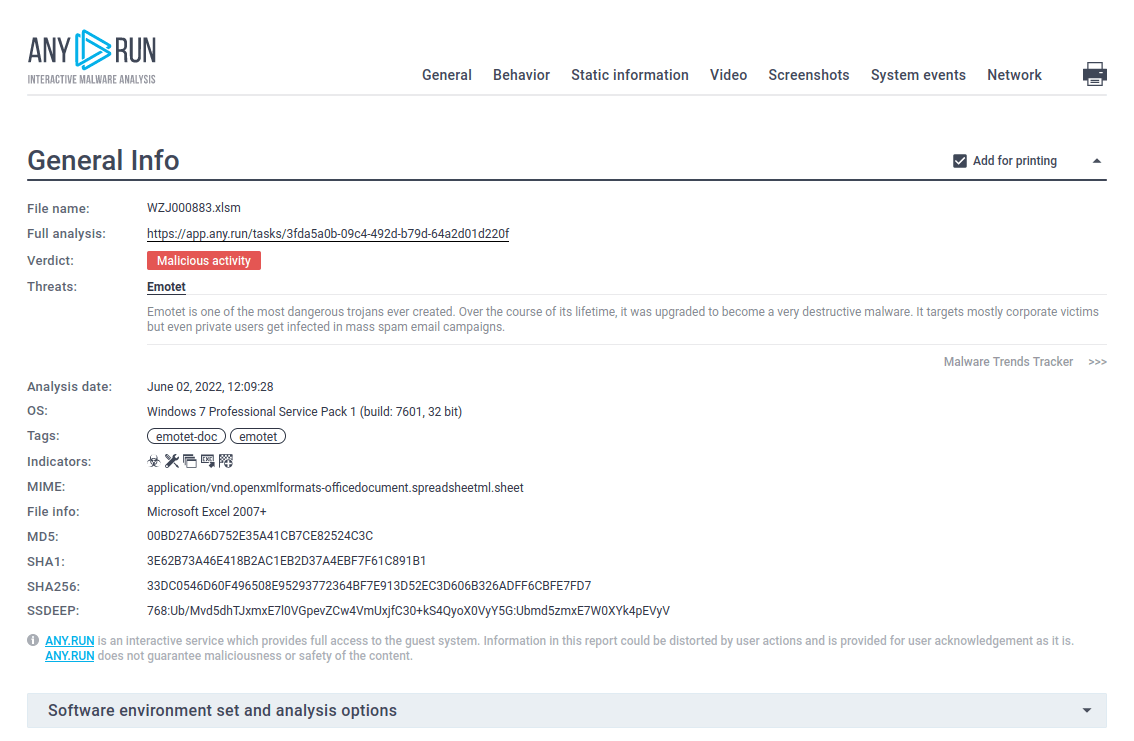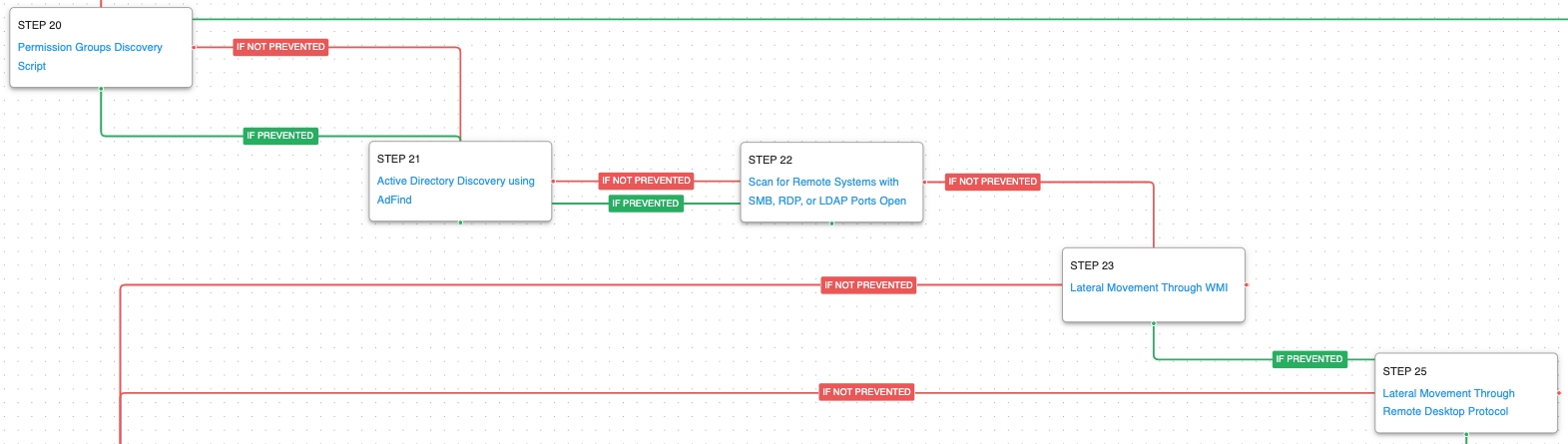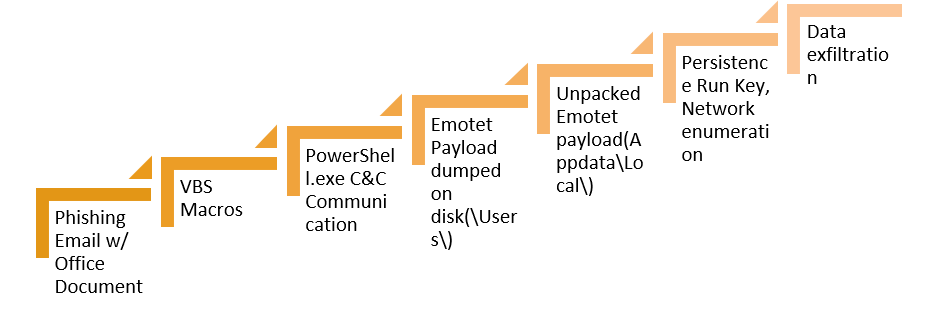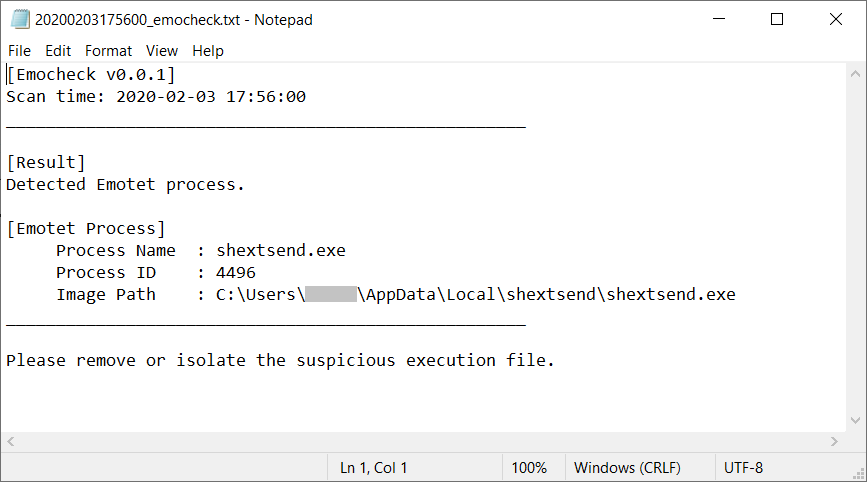
How to Respond to Emotet Infection (FAQ) - JPCERT/CC Eyes | JPCERT Coordination Center official Blog

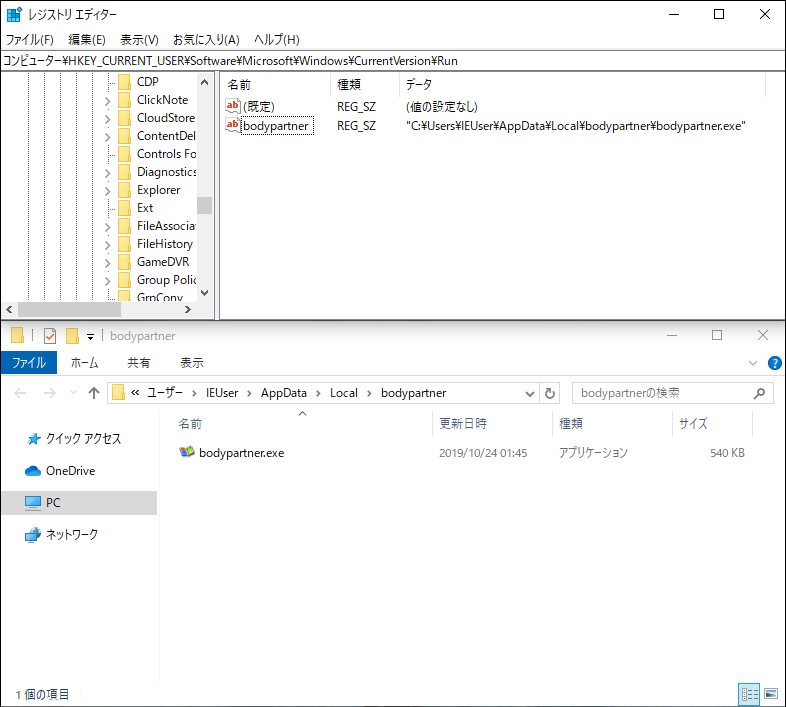
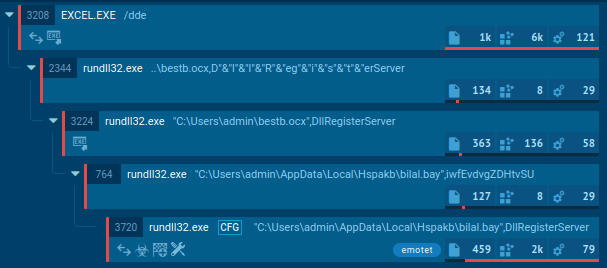
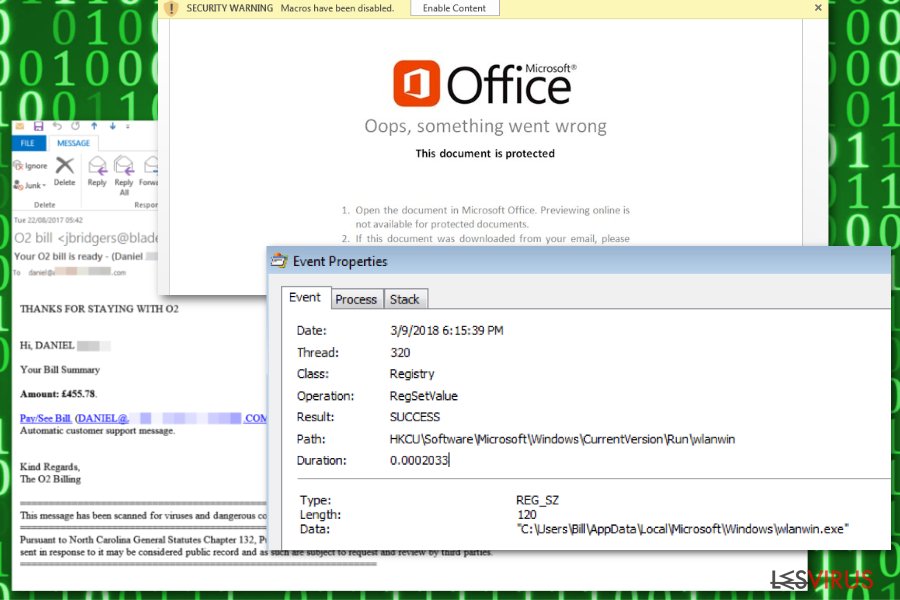
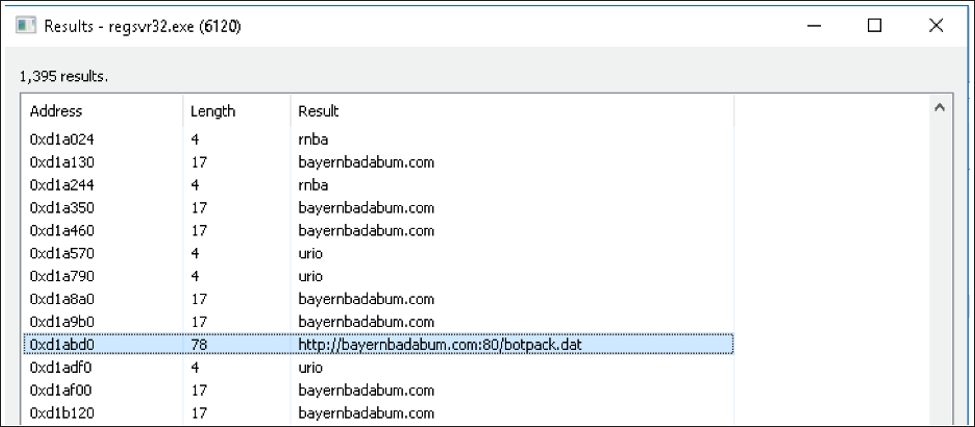
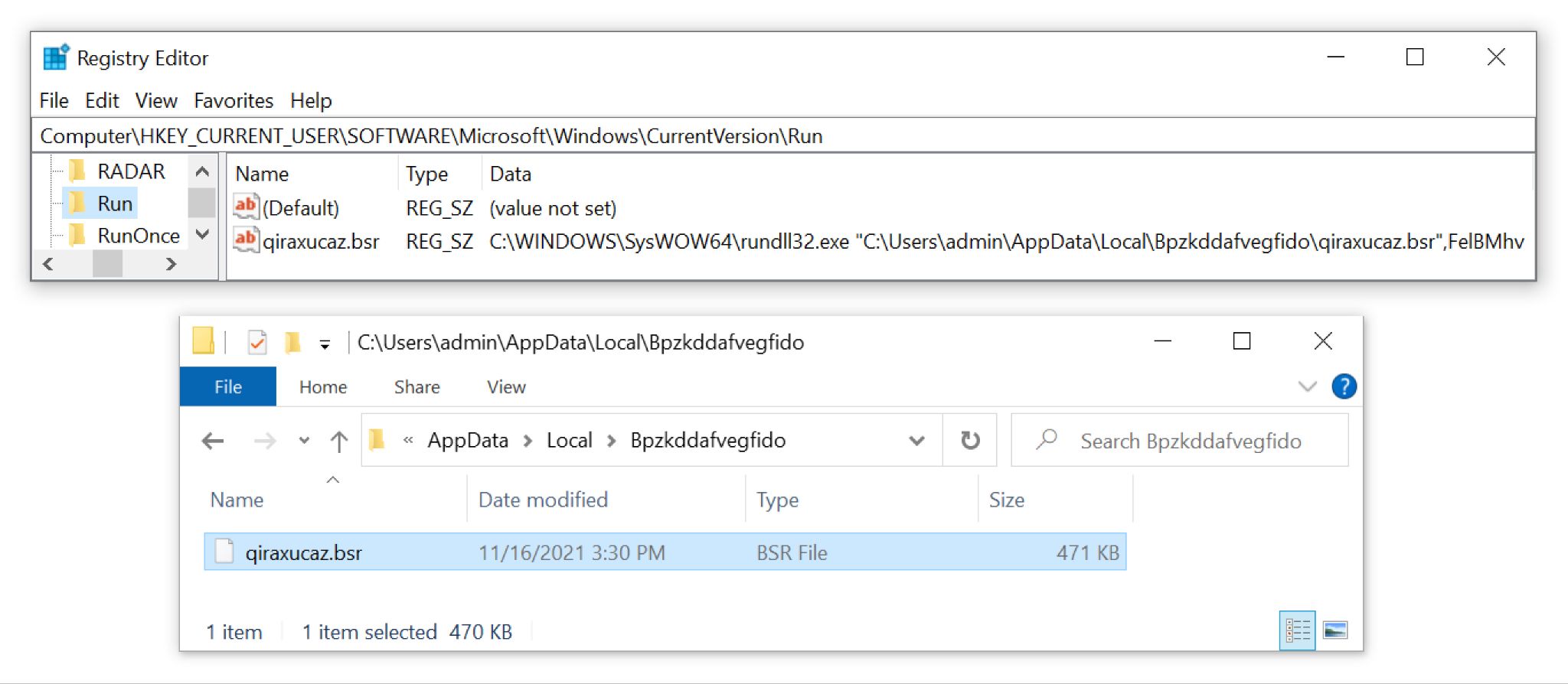
Germán Fernández on X: "RT @Max_Mal_: #Emotet - Persistence - Registry Run Keys (T1547.001) #DFIR Process: Rundll32.exe Registry Key: HCU\SOFTWARE\Mic…" / X

Germán Fernández on X: "RT @Max_Mal_: #Emotet - Persistence - Registry Run Keys (T1547.001) #DFIR Process: Rundll32.exe Registry Key: HCU\SOFTWARE\Mic…" / X

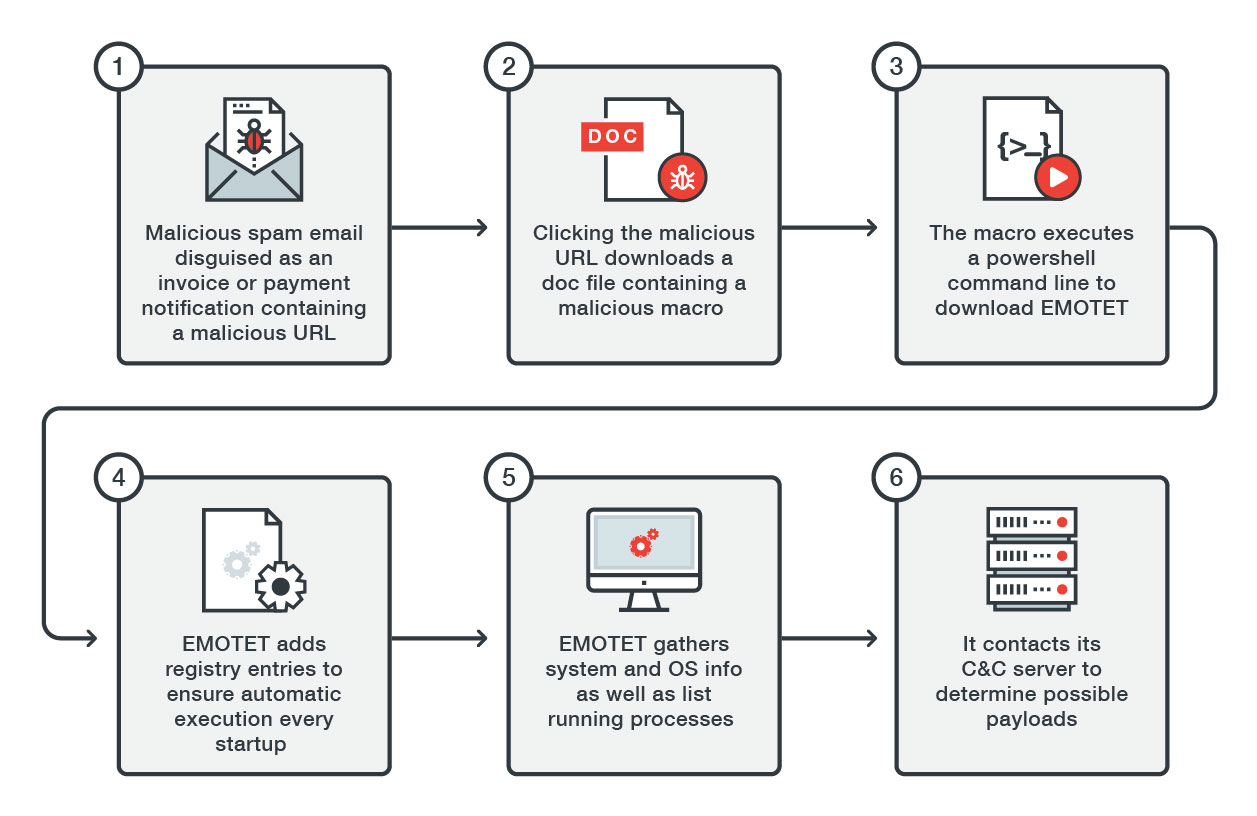
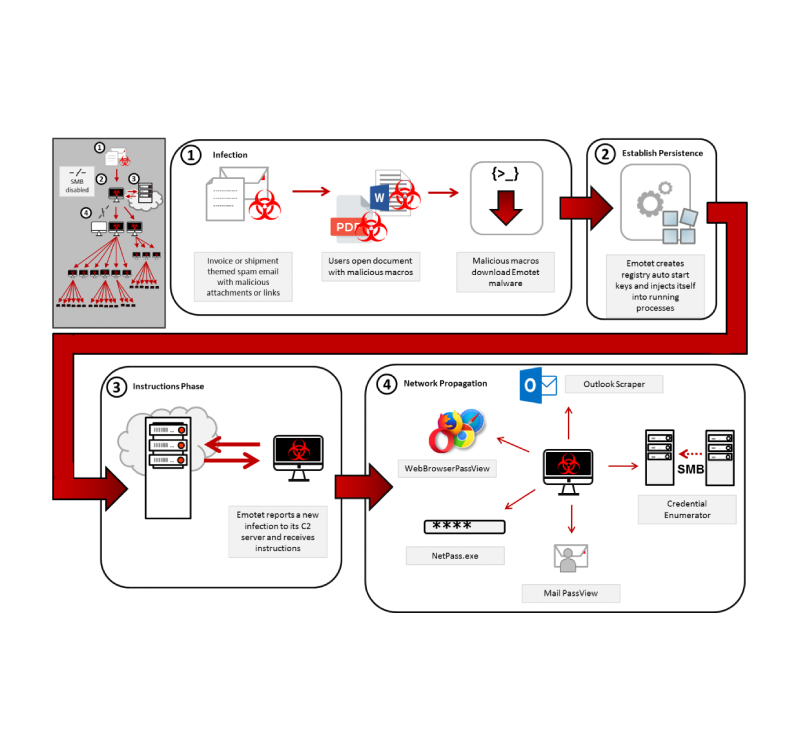
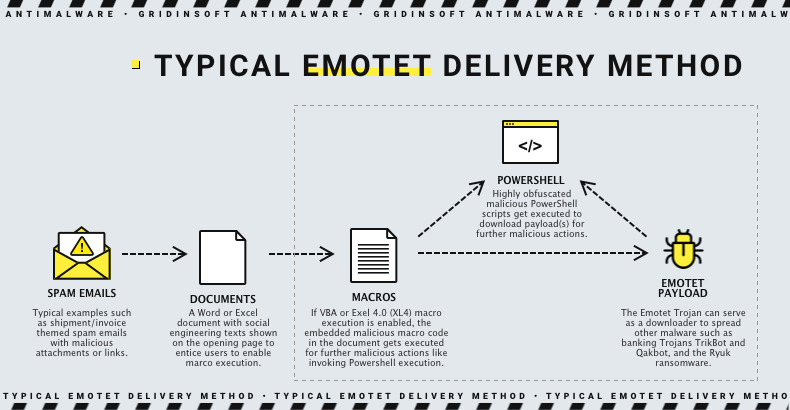
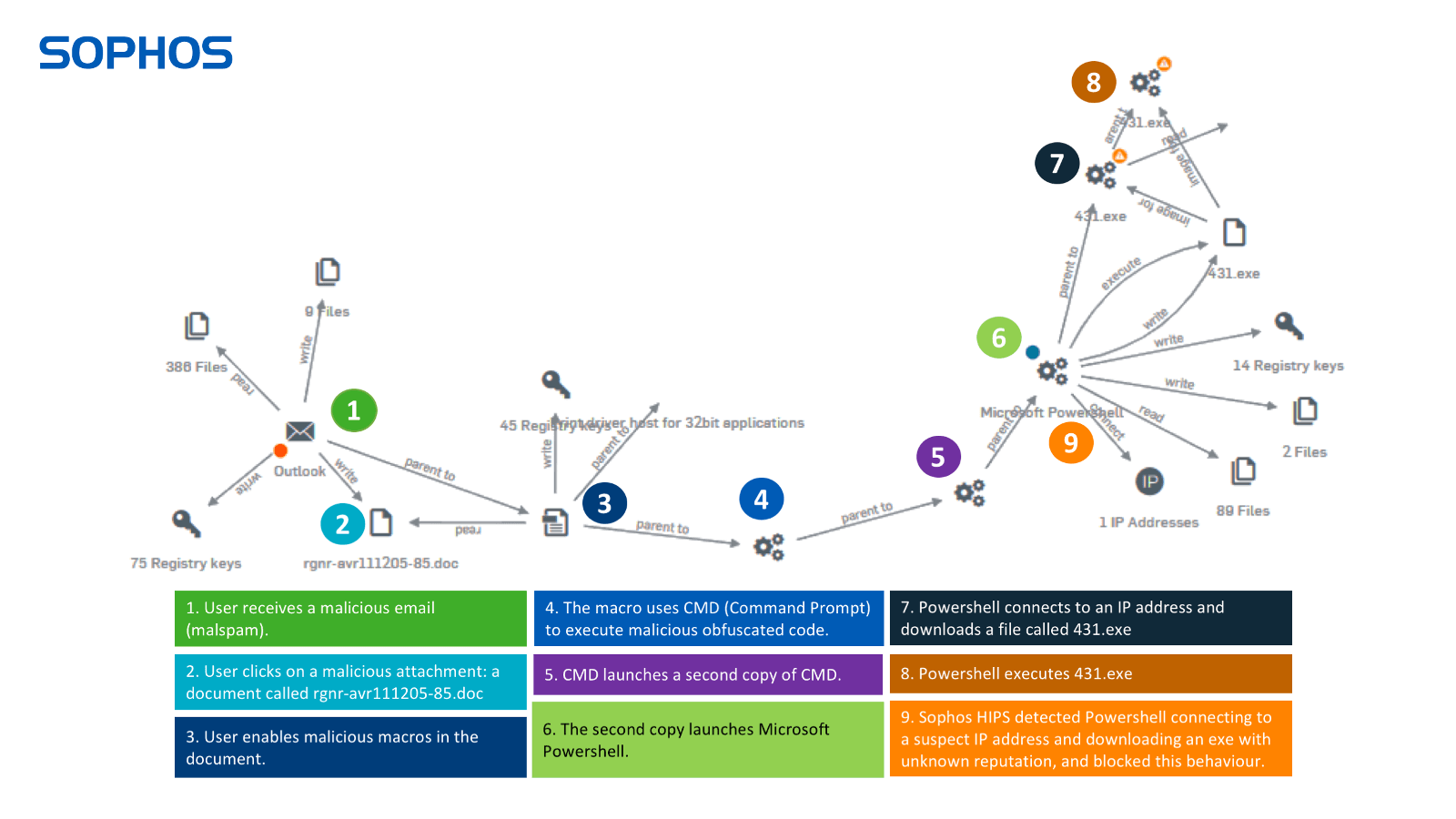
EMOTET – Informationen und warum es Sinn macht Libre Office zu verwenden – Willkommen auf imaginative.at B2B EDV-Dienstleistungen und IT-Dienstleistungen