GitHub - Tecatech/key-derivation-function: Tool for generating cryptographic keys using Key Derivation Function (KDF)

1 Standardizing Key Derivation Functions Hugo Krawczyk IBM Research Or: google kdf hmac. - ppt download

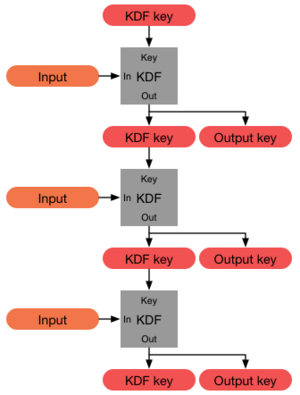
Signal double ratchet Key-Derivation Function (KDF) Chains; (reproduced... | Download Scientific Diagram



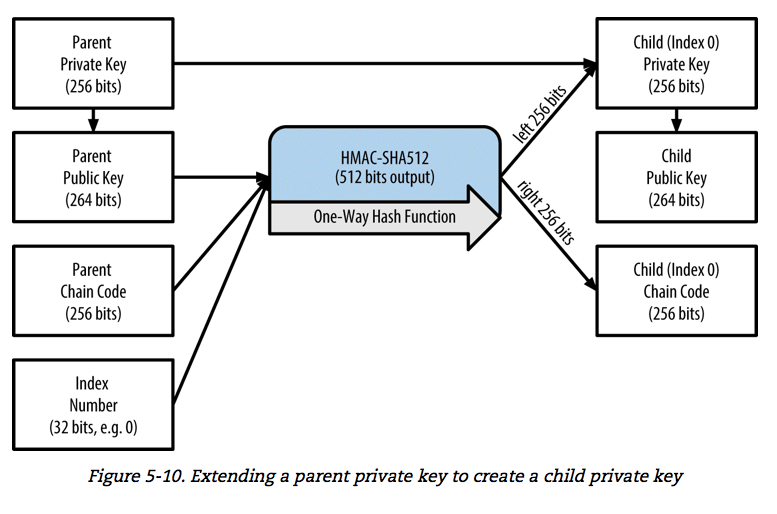
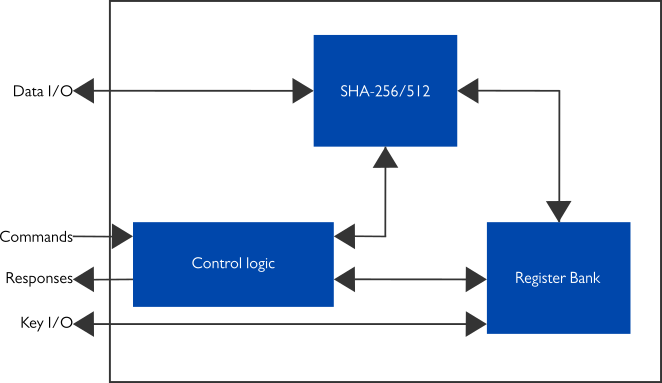
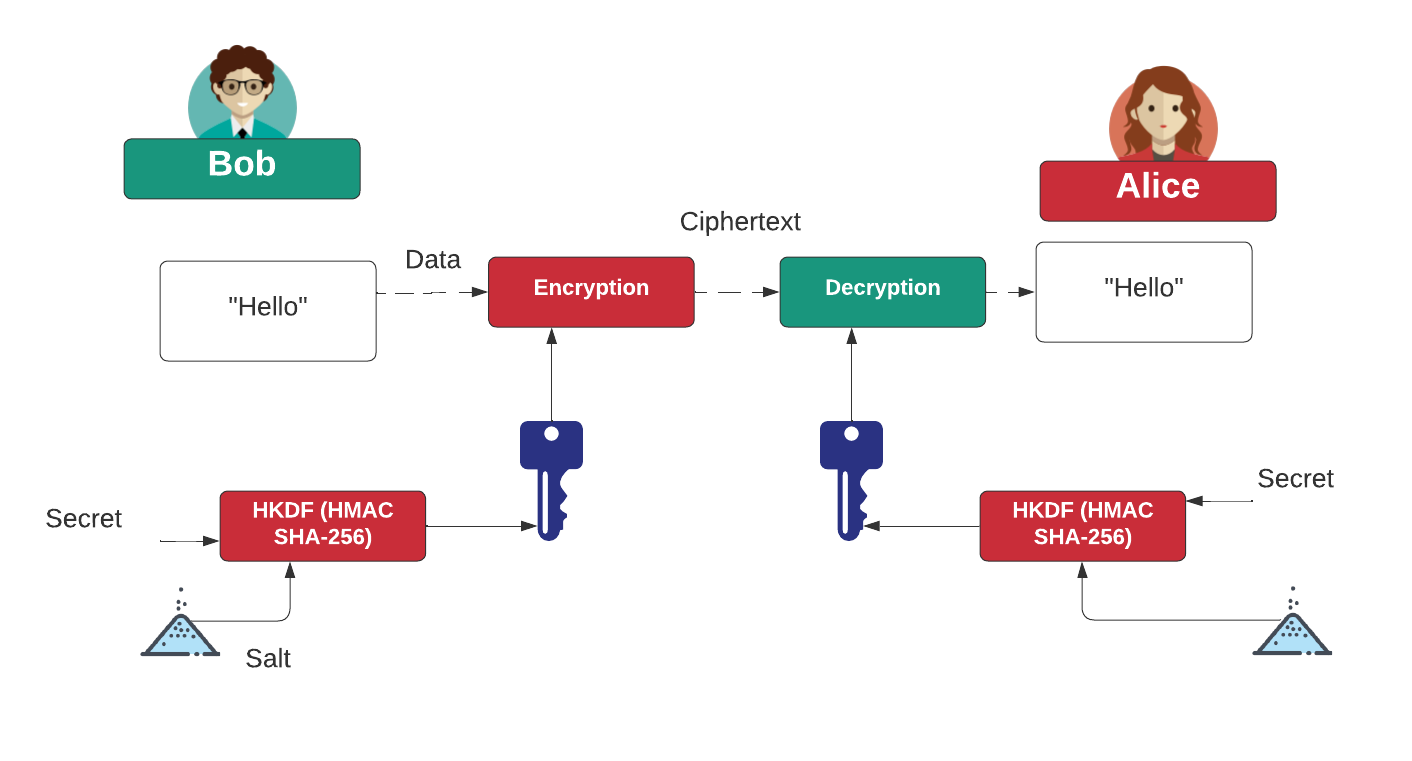
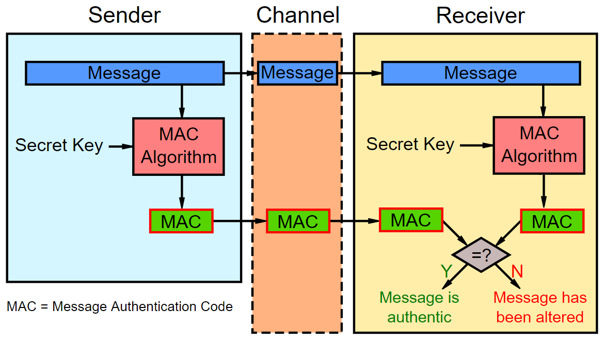

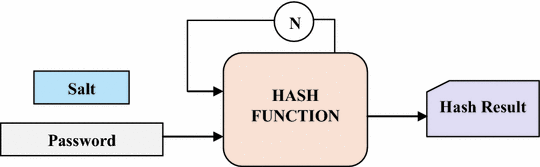


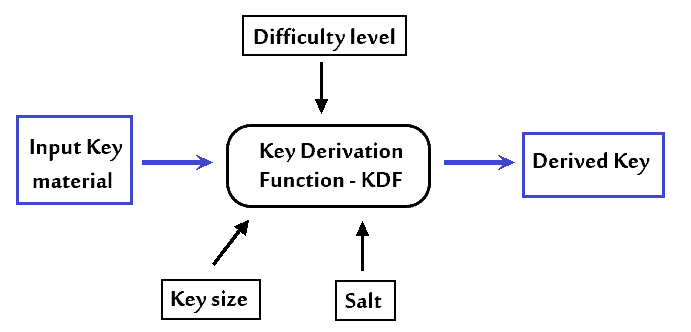


![Key derivation - Practical Internet of Things Security - Second Edition [Book] Key derivation - Practical Internet of Things Security - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788625821/files/assets/7e4474a1-658a-4b60-a90d-41fc615bd89e.png)