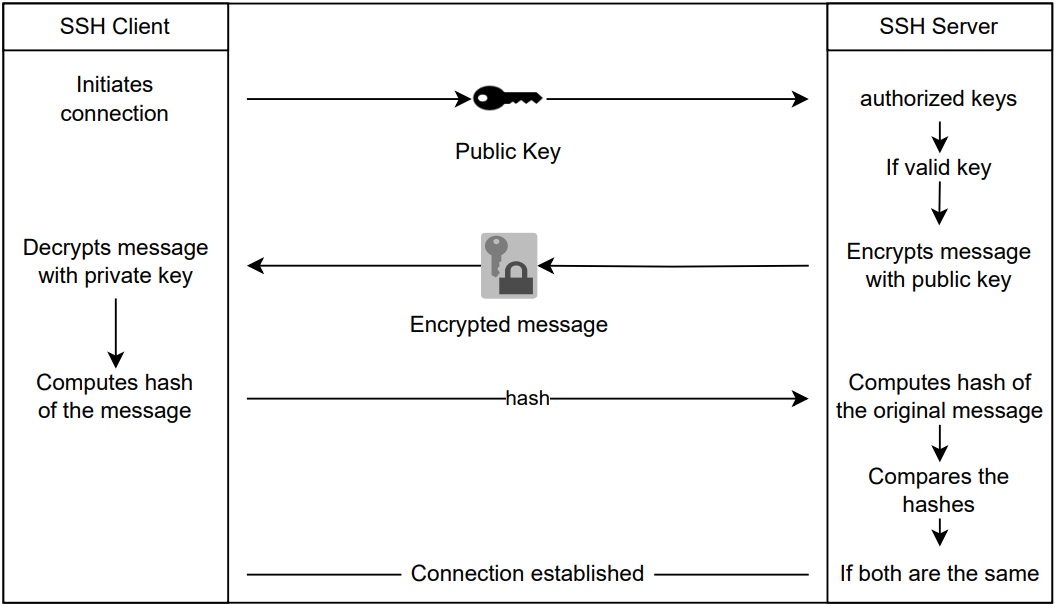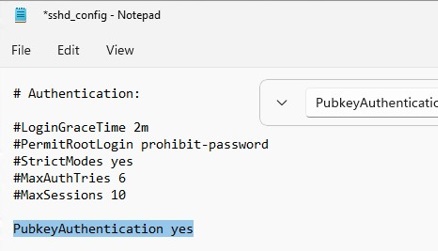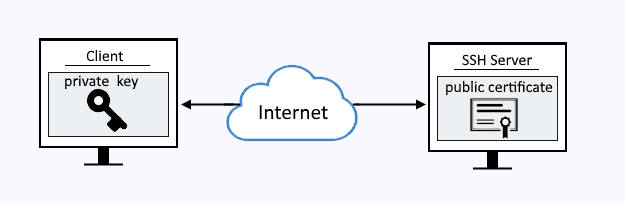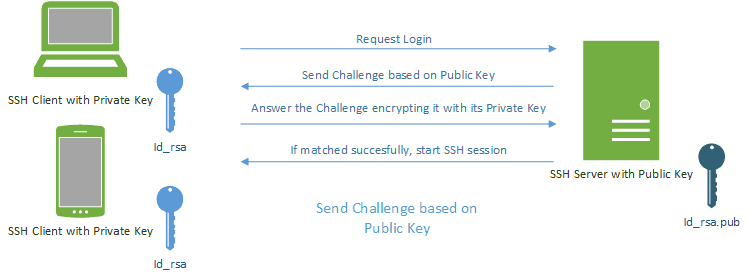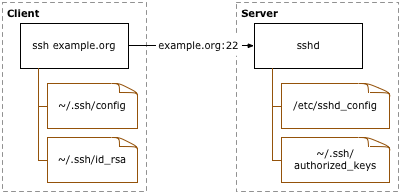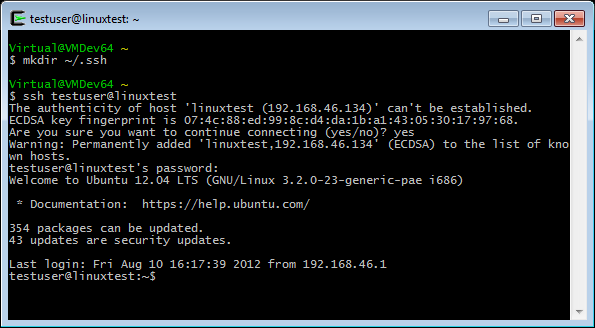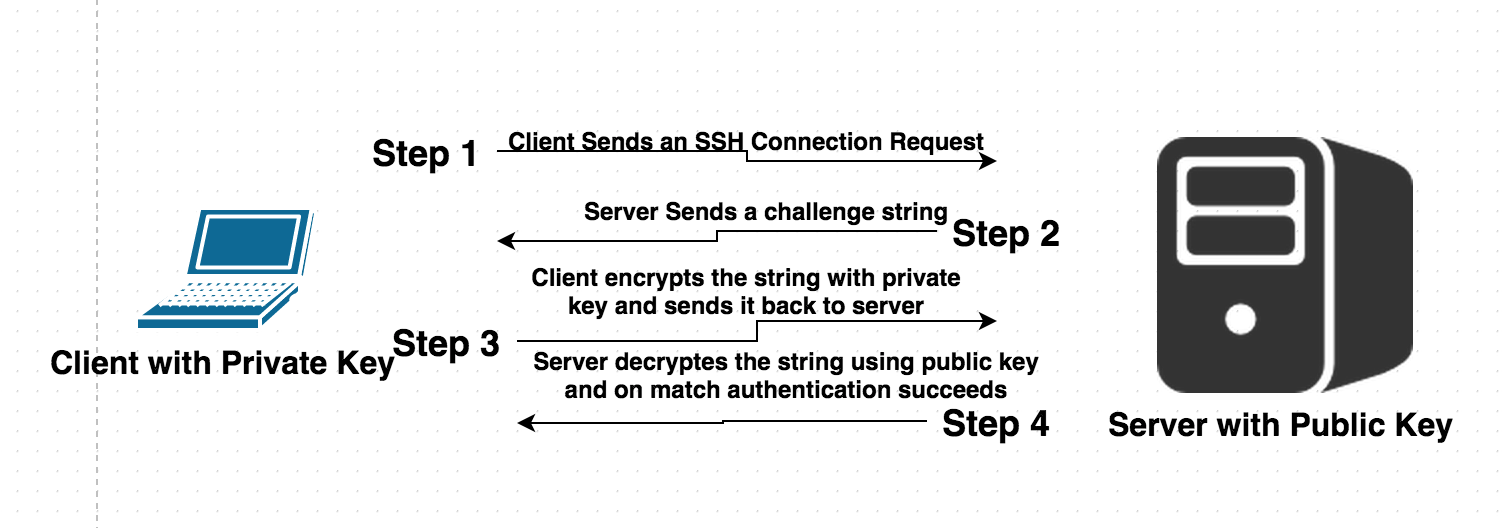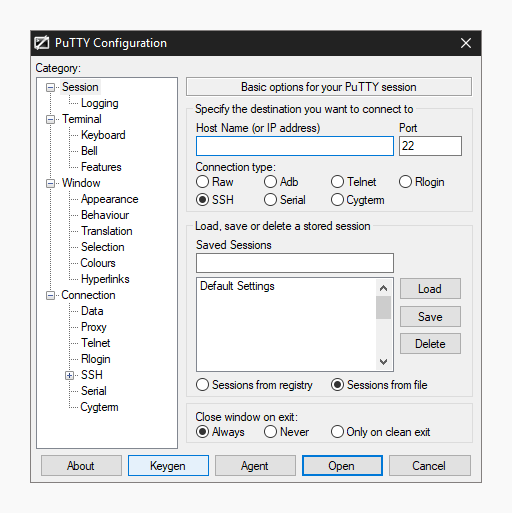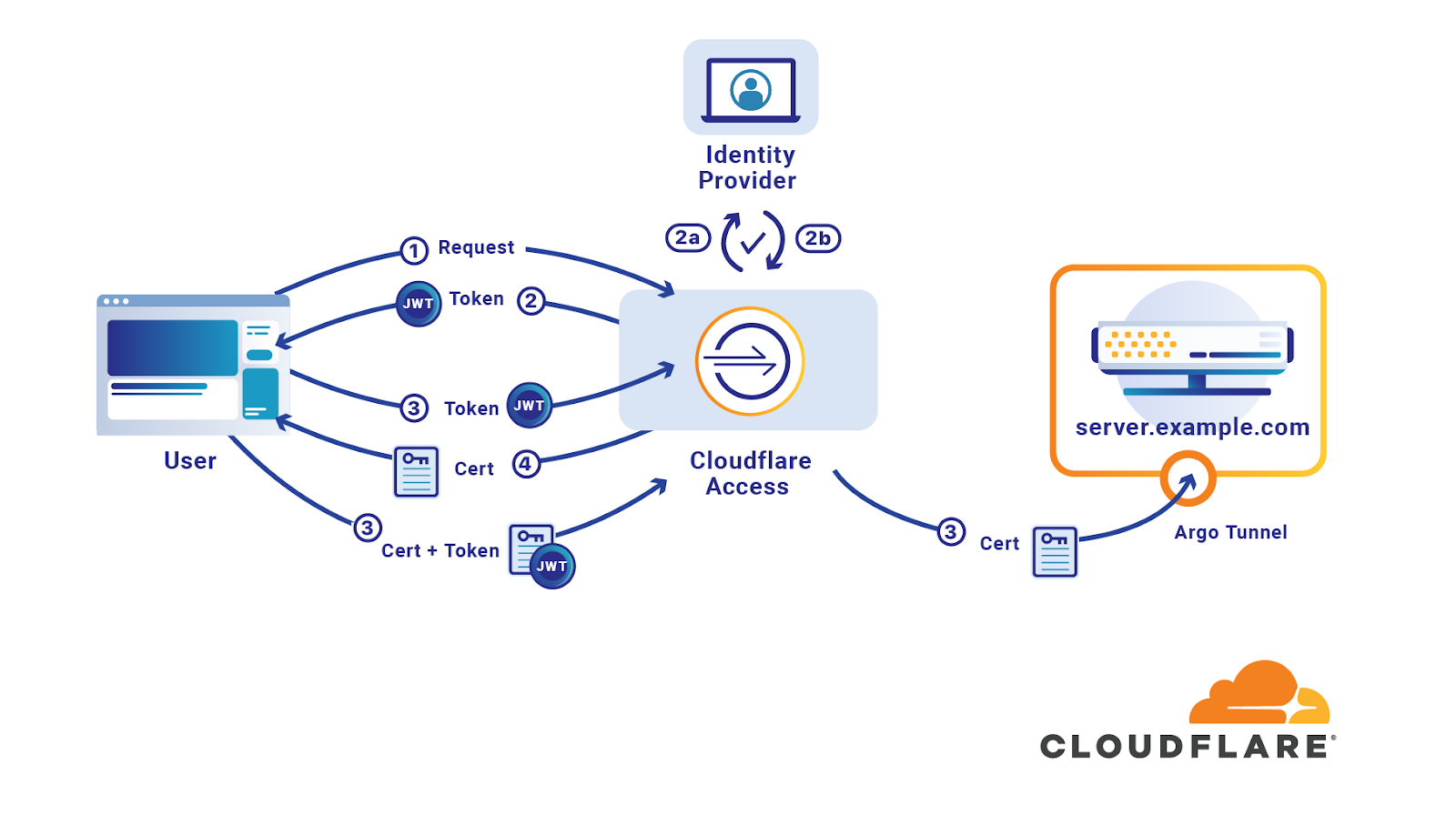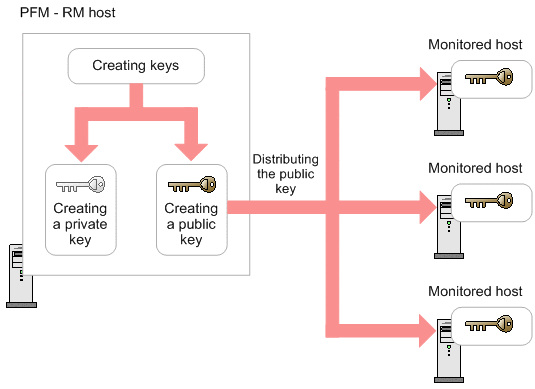
3.2.5 SSH (for UNIX) connection setting method : JP1/Performance Management - Remote Monitor for Platform Description, User's Guide and Reference
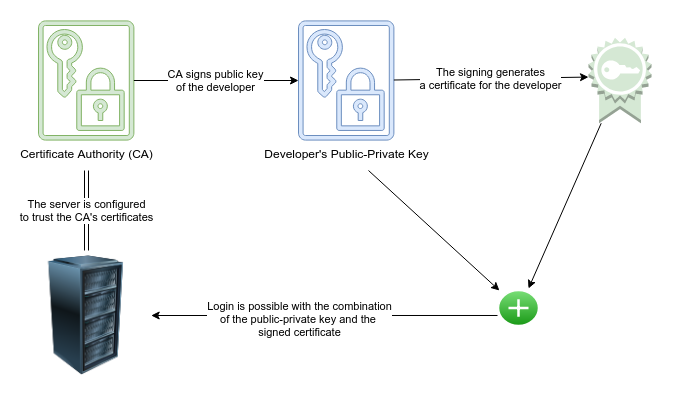
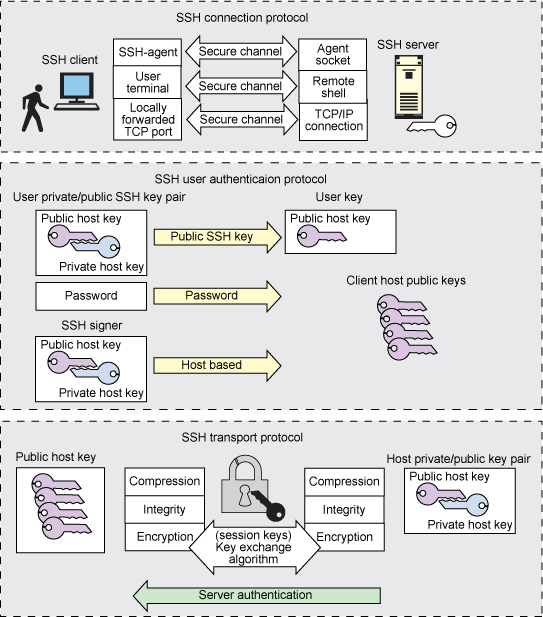
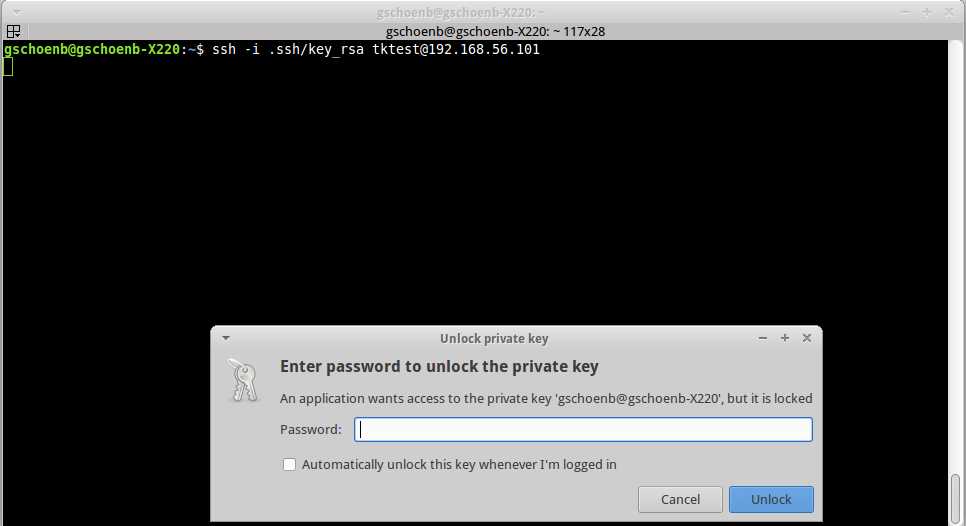
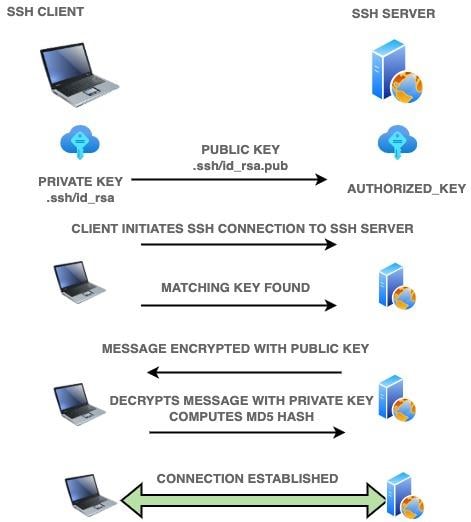
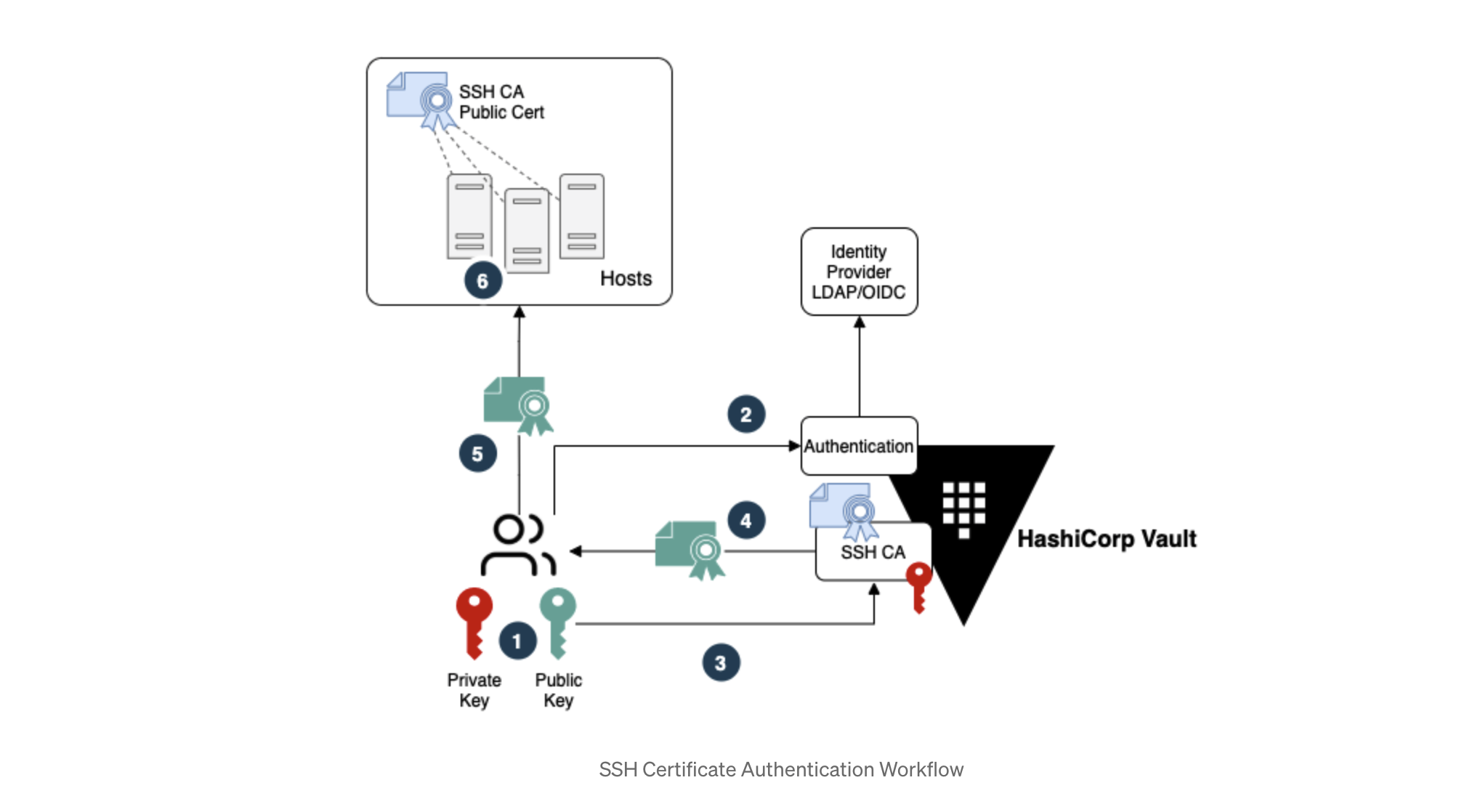
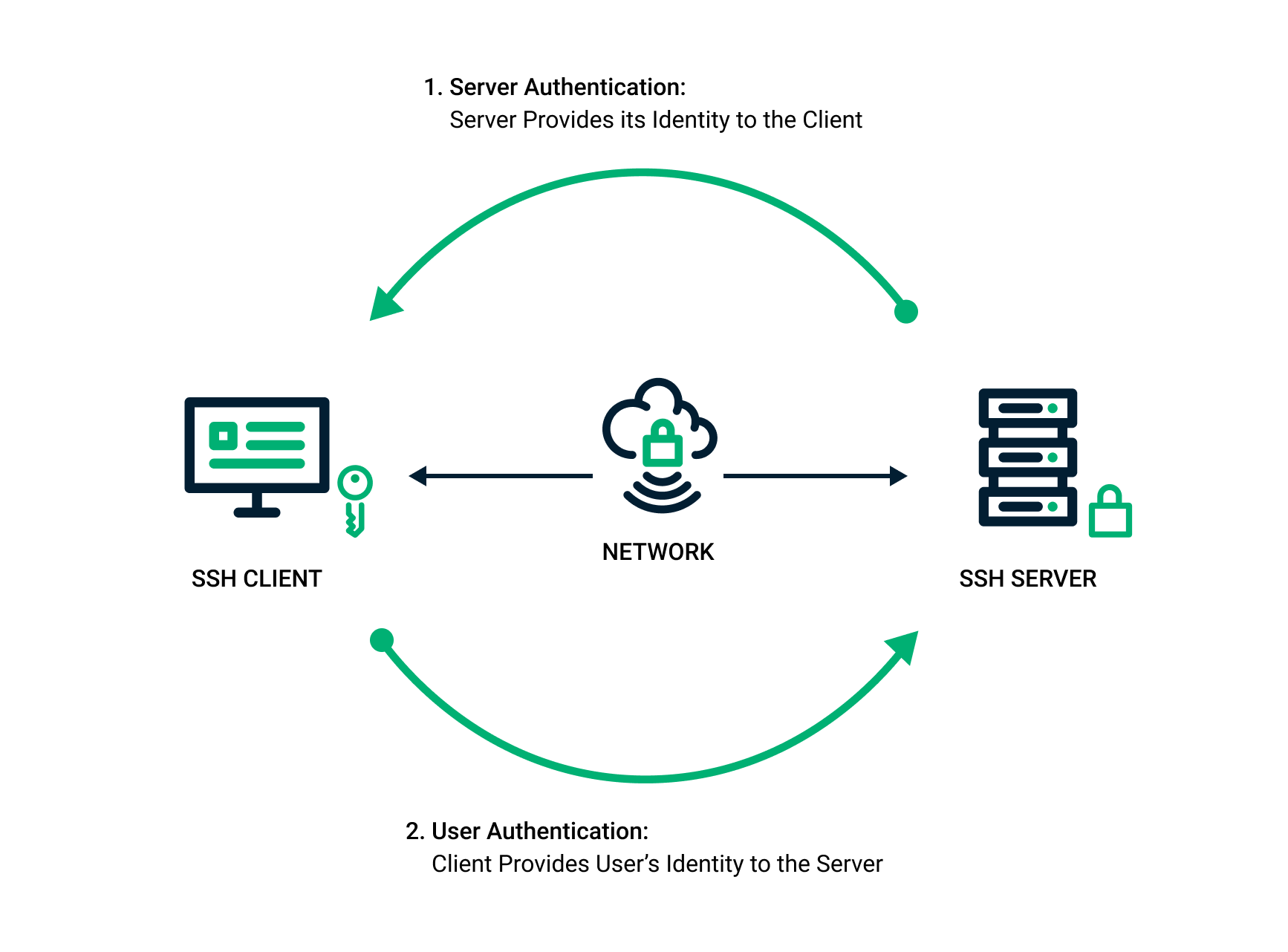
How to properly manage ssh keys for server access :: Päpper's Machine Learning Blog — This blog features state of the art applications in machine learning with a lot of PyTorch samples